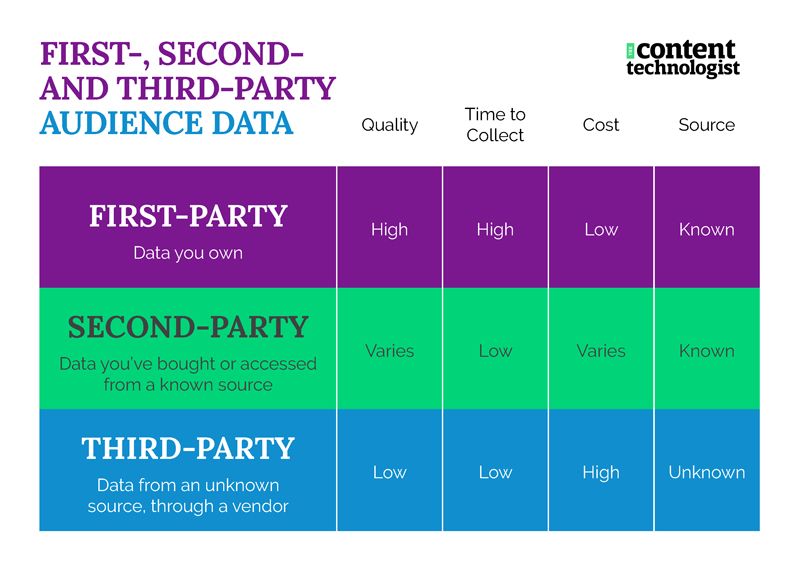
This essay originally was published on January 26, 2022, with the email subject line "CT No. 152: Hey, wanna cyber-secure your content business?"
I didn’t use to think much about digital privacy or security. I was a let-it-all-hang-out kind of internet user back then, with a public personal blog, an opinionated Twitter account, and a hopefulness about technology so naïve I wondered if getting a Google brain implant could be fun. My descent into what became an obsession and eventually a career in cybersecurity began in 2010 while working at WIRED. It was the heyday of Wikileaks and Anonymous; Adrian Lamo had just dumped the Manning chat logs to one of my colleagues at the San Francisco office, and Kim Zetter was unraveling the Stuxnet industrial malware story. Privacy and security were hot topics around the office, even though many of us still hadn’t adopted what are now commonplace security measures into our own workplace communication practices.
Then a colleague got mad at me for messaging them over GChat. It may sound paranoid, but they were overseas covering the Arab Spring. They had good reason to insist on moving our chats to a more secure channel. I got to thinking: maybe I should get better at understanding how being extremely online doesn’t come without risks.
Over the next 10 years I fell down the rabbit hole of cybersecurity questions and sought out an array of answers which only led to more questions. Cybersecurity experts, much like insurance salespeople, tend to linger excessively in the Valley of Worst-Case Scenarios. As James Mickens once wrote in his memorable 2014 essay, “This World of Ours” (pdf):
The only thing that I’ve ever wanted for Christmas is an automated way to generate strong yet memorable passwords. Unfortunately, large swaths of the security community are fixated on avant garde horrors such as the fact that, during solar eclipses, pacemakers can be remotely controlled with a garage door opener and a Pringles can.
We’re not going to the Valley of Worst Case Scenarios today. I’m not here to give you a panic attack or convince you to buy military-grade encryption software. My goal today is to make sure you, your company, and your audience aren’t low-hanging fruit for the hordes of very real hackers and data brokers out there looking for easy targets.
Threat modeling for content professionals
A threat model is a simple way to assess risks and viable responses as they apply to your situation. By creating a reasonable portrait of potential harm, you can also rule out solutions that will likely be overkill for your specific situation. Why buy a state-of-the-art safe if a simple padlock will protect you?
Here is a basic example of a threat model, also borrowed from Mickens:
Good news: Chances are, if you’re a subscriber to The Content Technologist, you are probably not engaged in Nation-State espionage, whistleblowing of classified information, or political dissent against a violent dictatorship. (And if you are, nothing in this essay should come as new information to you.) We can automatically rule out some of the more sinister Worst Case Scenarios. We also don’t need to get into some of the more complicated solutions, like wiping your laptop every time you cross a border and encrypting every email with PGP. Regardless, your work is very likely interesting to cybercriminals. Why? You're managing audience data, and lots of it.
Whether you’re deploying a digital content campaign to tens of thousands of customers, running marketing and user experience testing with third-party vendors, or managing content or social media production or operations, you should follow or implement company security protocols around user account management, access control, and authentication. You’ll want to ensure that your practices are not only legal but also respectful of your audience’s privacy beyond the law (i.e., don’t spam or otherwise abuse their trust in your brand).
Let’s explore some threats and solutions for the very real problems you could encounter in your professional life:
Potential security and privacy threats in content operations
We all know by now that reusing passwords is bad, data brokers are real, and data is valuable, so the potential threats we’ll consider for your industry mostly revolve around:
- Amateur hackers (or disgruntled ex-employees) gaining access to your or your employees' work email accounts. Hacking may not even necessarily be required: an unwelcome party can simply guess if you’re using a password from the very well-known list of most commonly used passwords. Even if it is a good password, if it’s been reused on multiple sites, and one of those sites had a data breach, that password is now part of a data set being sold or even just passed around on dark web markets.
- A third-party service you’ve signed up for misusing your audience data. I guess you Didn’t read the Terms of Service? Too bad. In the Wild West world of third-party software and browser extensions, vendors may use your data far outside of expected scenarios, or what’s necessary for use of the app.
Remember: the tools you choose are vendor partnerships, which means their choices around your audience’s privacy are the responsibility of your brand. You didn’t know you agreed to content scraping of your company's IP or keystroke logging? Live and learn. - Leaking a customer’s personally identifiable information, especially in a way which can be traced back to your company. You didn’t really think Slack conversations were private, did you?
- A third-party vendor selling your email list to another company. Selling lists or buying email lists remains a common practice in marketing, even though it never gets results.
- Inadvertently spamming your audience via email automation or text. You may or may not know why it’s happening, but regardless, every time a customer hits the “spam” button or files an FCC (or your country’s equivalent) complaint, it negatively impacts your digital reputation.
- A hacker (or disgruntled former employee) logging in to company accounts to wreak havoc on the socials or through your content management system.
Best practices and policies to keep company and audience data secure
If you can imagine one or more of the above scenarios happening to you, don’t worry; explore these solutions to cover your bases and rest assured:
- Check yourself: Have I Been Pwned?
- Password managers: Pick a recommended tool and use it to create strong, unique passwords for yourself and people with whom you manage or collaborate. “But what if someone steals the password to my password manager and gets all my passwords at once?” you’re surely wondering, as I did when I first fell down the cybersecurity rabbit hole.
- Multi Factor Authentication: Use it. And use it on your password manager as well.
- Biometrics: It may still seem a bit sci-fi, but using biometrics in conjunction with MFA may soon be the new normal. A group of cybersecurity experts called the FIDO Alliance is working very hard to incorporate biometrics into security standards (while mostly being ignored). They recommend a paradigm shift to “passwordless authentication” and blame passwords for 99% of havoc presently wreaked online.* If it’s easy enough for you to implement now, do it. Hardware companies will make it easier in the near future.
- Understand the structure and policies of your vendor partners. For example, does your newsletter service have a policy against copying your subscriber lists into their own system and spamming them willy nilly? Even some of the most popular newsletter services have been found to overreach. In terms of global software and user privacy, the tide is slowly turning from “no regulation” toward “some regulation.” But in the world of growth hacking and loosey goosey startup land, selling user data can be considered another revenue stream. Companies that embrace the practice call it growth hacking for a reason.
- Coordinate with your CTO/IT department around using or updating third-party tools. If you see a software update or other warning, let someone know. File bug reports if something isn’t working properly or seems phishy.
- Follow IT policies, even if they are a bottleneck. I know it’s easy to sign up for a SaaS mailing list service or put an ad pixel on a website without understanding whether your new tech complies with the company's values and ToS. If it doesn’t, you don’t want to be the one responsible for the brand and legal consequences.
- Remember that your audience's personally identifiable information, especially email addresses, should be protected. Create internal policies around data sharing, and evaluate the team members you trust with access to PII.
- Protect social media accounts and website content management systems with access management protocols that limit publishing power to administrators only. Audit who has posting access at least once a quarter and remove any accounts that no longer need access.
- Remember: Just because you can, doesn’t mean you should. Your audience’s data is your business. Protect it like you would your firstborn child.
If this seems like a lot, keep in mind that 10 years ago these solutions used to be difficult to implement and expensive. Now they’re cheap, bundled and easy. There are resources everywhere, and security researchers are auditing them all the time and releasing reports to advise about what tools follow best practices and uphold the highest standards according to a consensus of experts. Keep checking back though, because both the standards and the ranking of security tools change like the tides.
*It’s worth noting that Ghost, which hosts The Content Technologist and is a referral partner, uses passwordless authentication via a magic link. It’s not a perfect solution, but it’s a decent start. –DC
Pretty good security is good enough
If after reading this essay, you still have no desire to implement even the basic of solutions like changing your CMS admin password from “pizza123,” (I’m looking at you, FastCompany), remember that basic security administration is more fun than sending a legally required notice to your audience informing them you are responsible for the fact that their data is essentially public knowledge.
Get in shape with your security practices now to avoid consequences later. Your audience likely won’t thank you, because if everything goes right they won’t have to even think about your efforts. But if things go wrong, a customer exodus could be nigh.
Don’t let the fear creep in. Start loading those passwords into your security researcher–recommended password manager, clear your cache, and change your passwords as you log back in. You’ll be secure enough in no time.
Probably.
Arikia Millikan is a writer, editor, strategist, community manager and content technologist based in Berlin, Germany. She is the founder of CTRL+X, a consultancy which provides editorial strategy and services to companies specializing in niche technological topics like cybersecurity, biotechnology, and mixed-reality media. She previously founded LadyBits, Scientopia, and was an editor at WIRED.
Hand-picked related content